We live in a world where cyberattacks are inevitable, and this ‘not if, but when’ thinking is now directly affecting IT spend and prioritization. I have met with several IT professionals who have told me that their security budget, which previously was repeatedly rejected, now is a top priority for their senior leadership teams. I learned recently that one large health care organization has redirected their entire infrastructure spend to address current and emerging cybersecurity threat vectors. This is no coincidence. While the threat of a cyberattack is nothing new, the increased rate at which they occur is on the rise by a significant margin. In fact, a report from cybersecurity ventures quoted that ransomware is expected to attack a business, consumer, or device every 2 seconds by 2031.
This is a terrifying statistic given most companies are not yet where they want to be from a data security perspective as evidenced by the millions of cybersecurity job openings. Traditionally businesses have been focused on protecting data from power failures, system failures, natural disasters and some perimeter-level network protection. With a cyber-attack, more than just data needs protecting—at risk is really the entire physical infrastructure from applications and operating systems down to low-level firmware and BIOS. We’ve entered an era where IT infrastructure is materially more complex, distributed and harder to defend against today’s sophisticated cyber attackers, requiring an even more sophisticated protection, response and recovery solution than what was available even 2 years ago.
The state of the world today: where you’re covered and where you aren’t
If you’re looking to implement a cybersecurity strategy, a good place to start is to review the NIST Cybersecurity Framework and apply it to your specific infrastructure deployment. There are multiple layers of protection necessary when securing data center infrastructure–no single solution can do it all. Choosing best-in-class protection, detection, response and recovery solutions for each layer of your infrastructure layer is the recommended strategy.
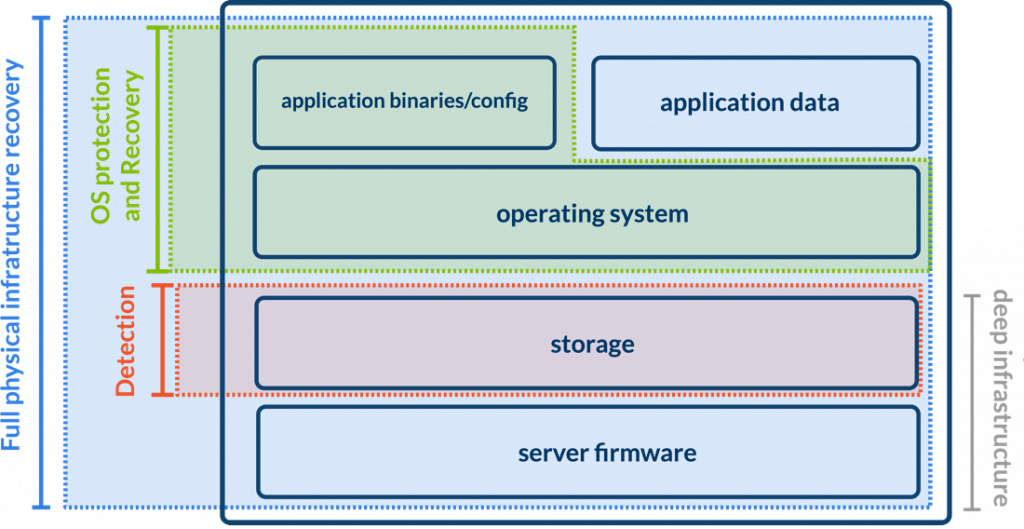
While several vendors already offer some really outstanding solutions to help protect, detect, identify, and recover across various layers, few operate at the ‘deep’ infrastructure layer. Deep and shallow infrastructure operations within multi-vendor data centers are important elements in maintaining the health and security of the IT operating environment. Shallow infrastructure is the stuff that is easy to do, essentially from the operating system up to the application stack, and many solutions and vendors are available to manage it today. The deep infrastructure operations is the difficult part, and sophisticated cyber-attacks have taken advantage of out-of-date software revisions to infect physical infrastructure.
APPLICATION INFRASTRUCTURE

According to a global survey from Microsoft, more than 80 percent of the firms surveyed experienced a firmware related attack in the past two years. Further validating the point is that 70 percent of organizations that lack firmware upgrade plans will be attacked as a result of a firmware vulnerability by 2022 according to Gartner.
All infrastructure needs to be cyber-resilient
These statistics demonstrate that your protection, detection, response and recovery strategy are only viable when the critical layers in the infrastructure have the appropriate data security technology in place. And, simply put, all infrastructure layers are critical, including deep infrastructure layers, when needing to recover from an attack with the least amount of damage (or cost) as possible. The best way to achieve this is with infrastructure that is cyber-resilient by default, which I examine in further detail below.
3 essential elements of cyber-resilient infrastructure
1. Immutable Infrastructure (OS & Deep Infrastructure Firmware) Protect
Infrastructure operations teams have spent years attempting to keep their software up-to-date with the latest flood of patches and firmware in an effort to remove vulnerabilities in the different layers of their infrastructure. However, as most of us know, this is a burdensome task. Managing each update with its own unique set of dependencies requires a level of planning and precision that infrastructure operations teams too often don’t have the time or bandwidth to complete, which means that deep infrastructure is often neglected.
We can look to the public cloud, more specifically Immutable Infrastructure, as an example of how to eliminate the complexity and anxiety associated with infrastructure updates. The simplest way to think about Immutable Infrastructure is that you don’t make changes to your infrastructure stack, but instead deploy a new stack from a golden image to completely replace the existing one.
Bringing this concept to your physical infrastructure means you no longer change individual aspects of your server-storage stack, you are no longer applying firmware updates, patches, drivers, application binaries, etc. individually. Instead, you deploy an updated, well-tested, and well-known stack from an image that includes updated firmware, operating system, binaries and configuration. Now, your server-storage deployment, apart from application data, becomes an immutable unit that you can easily secure, deploy and operate consistently and predictably.
How does this relate to cyber-resiliency? Being able to centrally design, harden and test your ideal stack and then making it immutable, means you have a known, good source for deploying your infrastructure, and you have reliable means to maintain this state indefinitely, whenever and wherever you want. If you know what you are running, you know what is vulnerable and what is not. If there are gaps, you can fix them easily by constructing an updated golden image centrally and rolling it out across your estate. If this sounds familiar, it is the container approach used in modern cloud applications, such as Kubernetes, but applied to the physical infrastructure layer.
2. Ransomware Detection Detect
There is something special about ransomware in the broader scheme of cyber-resiliency as it best portrays the current level of threats in IT. There is an undeniable surge in ransomware threats that infrastructure and operations teams need to arm themselves against.
The good news is that in a cyber-resilient infrastructure, ransomware cannot hide when it is attacking (encrypting) your application data, operating system or configuration data as it must pass the storage layer. Moreso, when it reaches the storage layer, all other means of protection at higher levels, i.e. operating system and network perimeter have failed. With monitoring and analytics capabilities on the storage layer, you can identify attacks quickly, precisely when and where the attack happened, allowing you to limit infection, narrow down the scope of recovery and minimize the amount of data loss.
3. Ransomware Recovery Recover
Rapid recovery is an essential element of a cyber-resilient infrastructure. Most if not all infrastructure vendors offer a recovery solution and rely on capturing snapshots or backups of the application data to recover. While this helps, recovery of application data is not enough.
Your applications are built as a layered stack of software–as indicated by my illustration above. In order to reliably recover, you’ll need to recover from the bottom up. To recover storage, your firmware must be healthy; to recover your operating system or application data, your storage must be operational; to access your application data, your operating system needs to be recovered… you get the idea. So, in order to become fully operational, you’ll need rapid full stack recovery. And remember that the scope of recovery depends on the scope of attack. An attack on firmware causes any layer above to be untrustworthy and you’ll require recovery at the deepest infrastructure levels. An attack on individual files can be accommodated by simple snapshot or backup restores. So, being able to recover on any infrastructure layer is a critical property of cyber-resilient infrastructure.
How we deliver it: smartInfrastructure, a cyber-resilient cloud operating platform
Nebulon has developed cyber-resilient cloud operating platform for on-premises infrastructure that allows CISOs/CIOs to address the elevated threat of ransomware as well as achieving the same efficiencies, and user experience, as the public cloud for their on-premises infrastructure deployments. With this approach, Nebulon extends the cloud operating platform concept in a number of ways specific to the needs of the enterprise and non-hyperscaler cloud service providers. Read our smartInfrastructure value paper to learn more.


